How does the watermark work?
In a nutshell? It’s invisible information that is woven into the color and brightness of the video’s pixels.
A computer can read back the information, but the human eye usually doesn’t notice it.
What is forensic watermarking?
Forensic watermarking is the process of hiding identifying information in each individual copy of a video file (read our whitepaper about the topic). A good watermark, like Custos’, is almost entirely imperceptible, impossible to remove without also damaging the host video, and secure – it cannot be faked or modified.
In the past, only the largest studios and distributors could afford forensic watermarking. Custos now makes this security technology easy to use and affordable for even the smallest video producer. The watermarking is also fast: the time-consuming video processing is done only once; after that, any number of individually watermarked copies can be created almost instantaneously.
Forensic watermarking is quickly becoming ubiquitous in the digital media rights management industry, but it is not new.
Analog watermarks date back to the 13th
Since then, the use of session-based forensic watermarks has become a common way to track the source of infringed content.
The following characteristics are desirable for forensic watermarks:
- Imperceptibility: A forensic watermark should not be audible or visible. To a human, a forensically watermarked media object should be indistinguishable from the unwatermarked original.
- Robustness: Even if an attacker knows that a media object is watermarked, it should be infeasible to remove the watermark without unacceptably damaging the host media in the process.
- Capacity: A good forensic watermark is capable of storing a large payload, as measured in bits of information.
- Security: It should be infeasible for an attacker to modify the payload of the watermark, or create a falsely watermarked media object.
- Efficiency: It should take as little computational time as possible to embed and extract the watermark into and from a media object.
How Custos’ Forensic Watermark Works
Custos provides a session-based forensic video watermark that is specifically designed to be readable by a publicly available extractor tool.
The watermark is built to be highly imperceptible (even in high dynamic range content), robust against the most destructive attacks like heavy video compression and “cam ripping”, and very fast to embed. It also has an exceptionally high payload capacity of 256 bits.
An application called Privateer is used to extract the watermark. After the video is downloaded, Privateer scans the video file frame-by-frame and builds up the payload. Forward error correction is used to repair damage caused by potential attacks.
For a watermark to be read reliably, “video registration” needs to be performed first, which is the reversal of clipping, rotation, timescale adjustment, and other reversible transforms. Independent software tools are available to do this, and Custos’ use of “bounty hunters” who voluntarily scan for watermarked content, puts “humans in the loop” who can intelligently reverse attacks to successfully read the watermark to claim a reward.
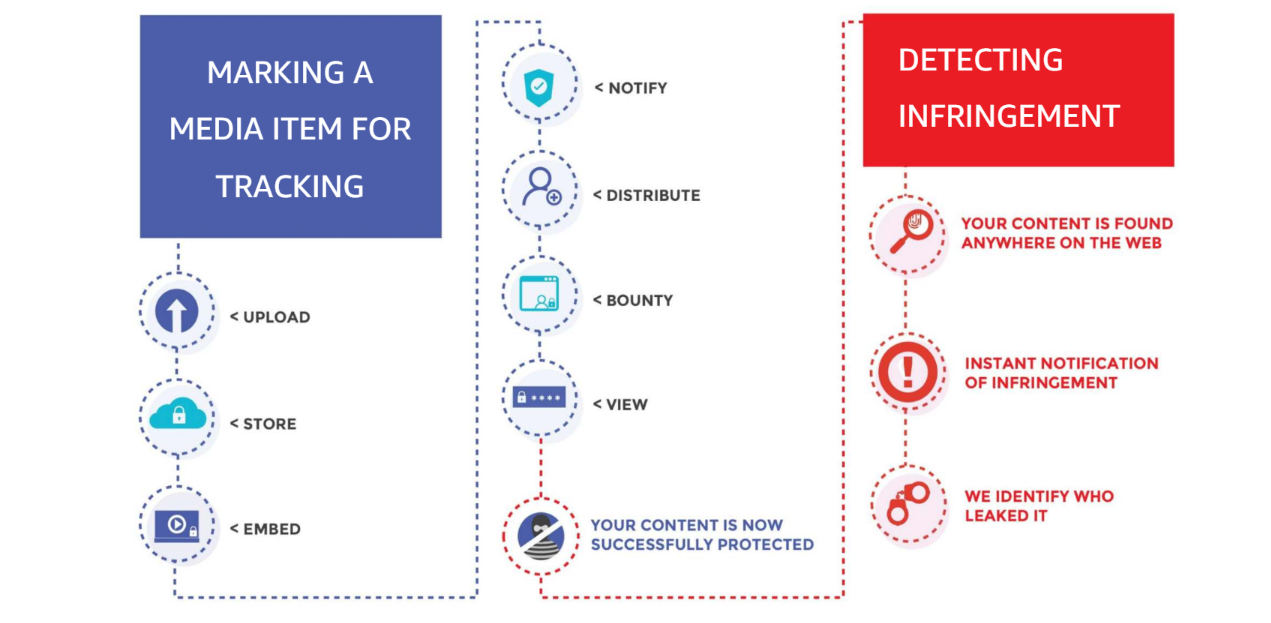
This poses a major improvement over visible watermarking. If a copy of a movie is found online, it can be traced back to the intended recipient, and this person can be prosecuted, excluded from future distribution, or otherwise sanctioned. The real power, however, is not as much in the tracking of infringement as in the deterrent effect that this so-called “social DRM” has on would-be pirates.
This social part of the DRM that plays into the incentives of would-be pirates is also the feature that sets it apart from conventional hard DRM in terms of appeal – both to end users and rights holders. Hard DRM attempts to block redistribution of content by technical means. This can be anything from copy protection on physical media, to web players that do not allow you to record the screen. The problem with this approach in terms of protecting against piracy is that sophisticated pirates will always be able to circumvent it.
